# 安全软件导致系统卡顿
# 问题背景
用户使用oa时偶发出现页面空白,无法正常访问(同一时间涉及大量用户),持续一段时间后自行恢复,如图
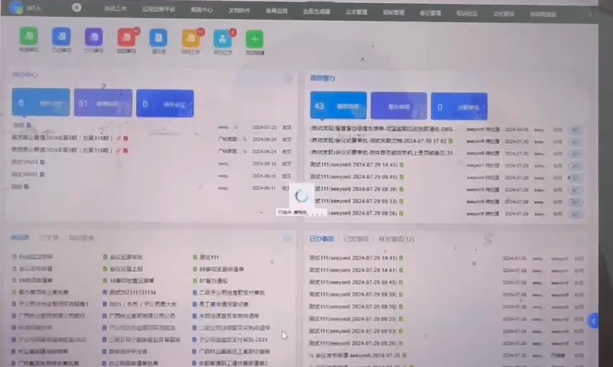
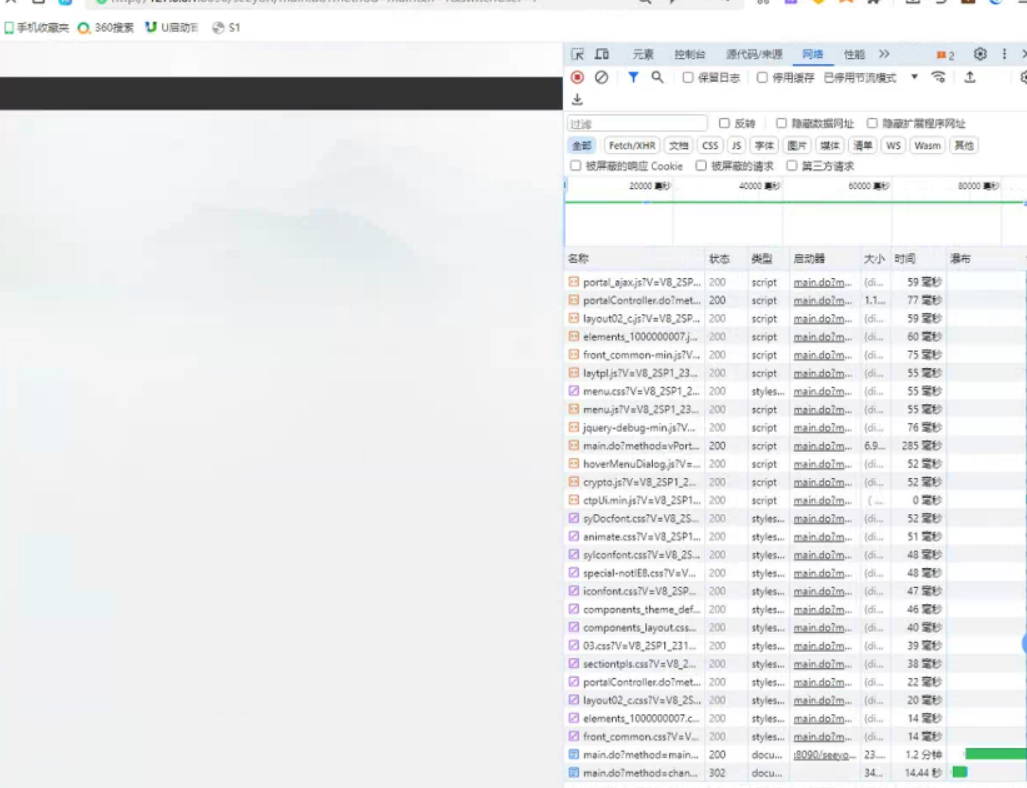
# 排查步骤
从上图访问地址为 http://127.0.0.1:8090 可知,oa卡与客户端到服务器之间的网络没有关系,是后端oa自身的问题
登录oa系统管理员账号后台,打开 系统维护——系统监控 页面,检查jvm堆内存使用情况,gc状态,连接池与线程数
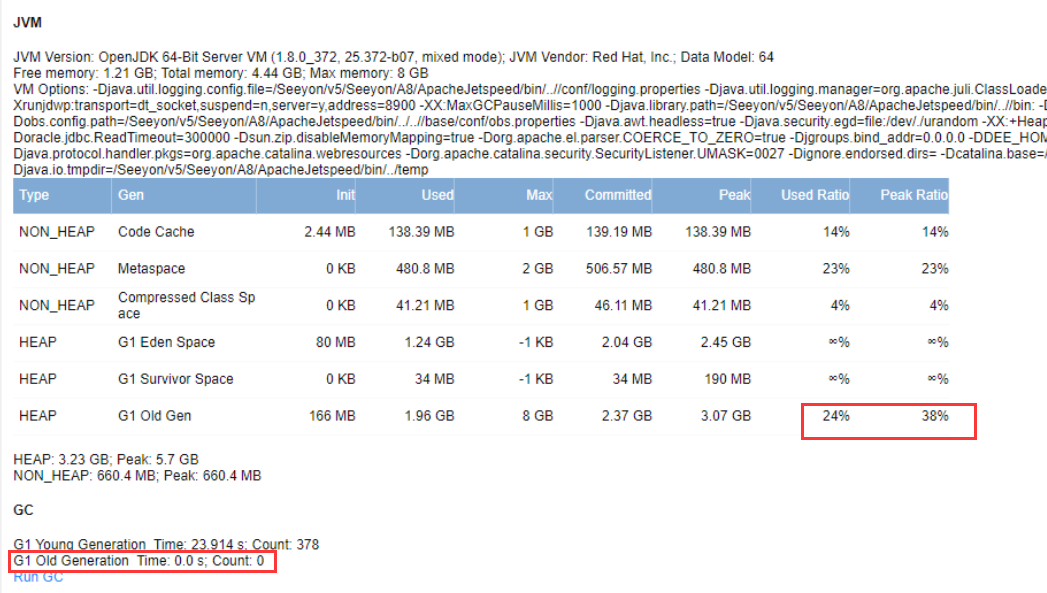
oa堆内存老年代使用率峰值不足40%,GC时间次数正常,服务器资源充足 但数据库连接峰值数较高,约90左右;线程池活动线程数也较高
- 导dump分析,较多线程卡在java.net.SocketInputStream.socketRead0(数据库)、java.lang.Throwable.fillInStackTrace、sun.nio.ch.SocketDispatcher.write0
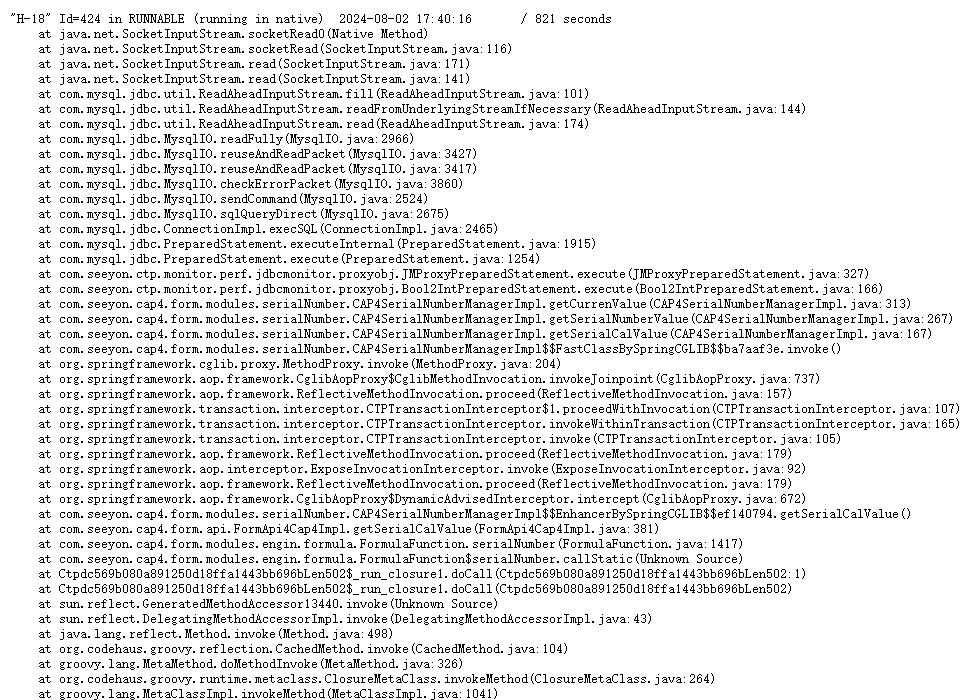
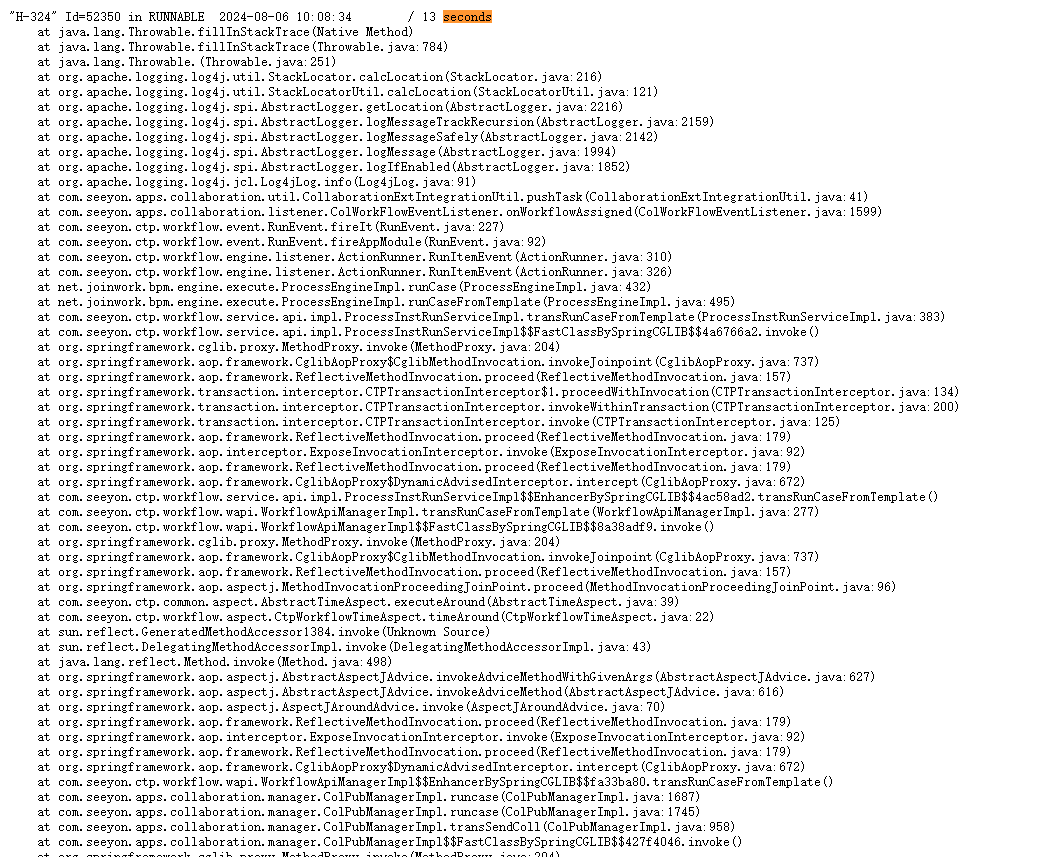
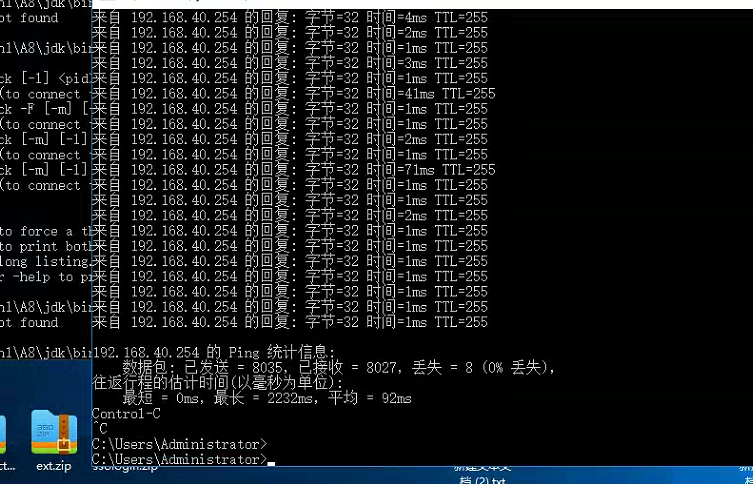
- 服务器上安装有360安全卫视;同时卡顿时查询数据库没有发现活动会话,ping数据库地址有较多延迟且存在少量丢包
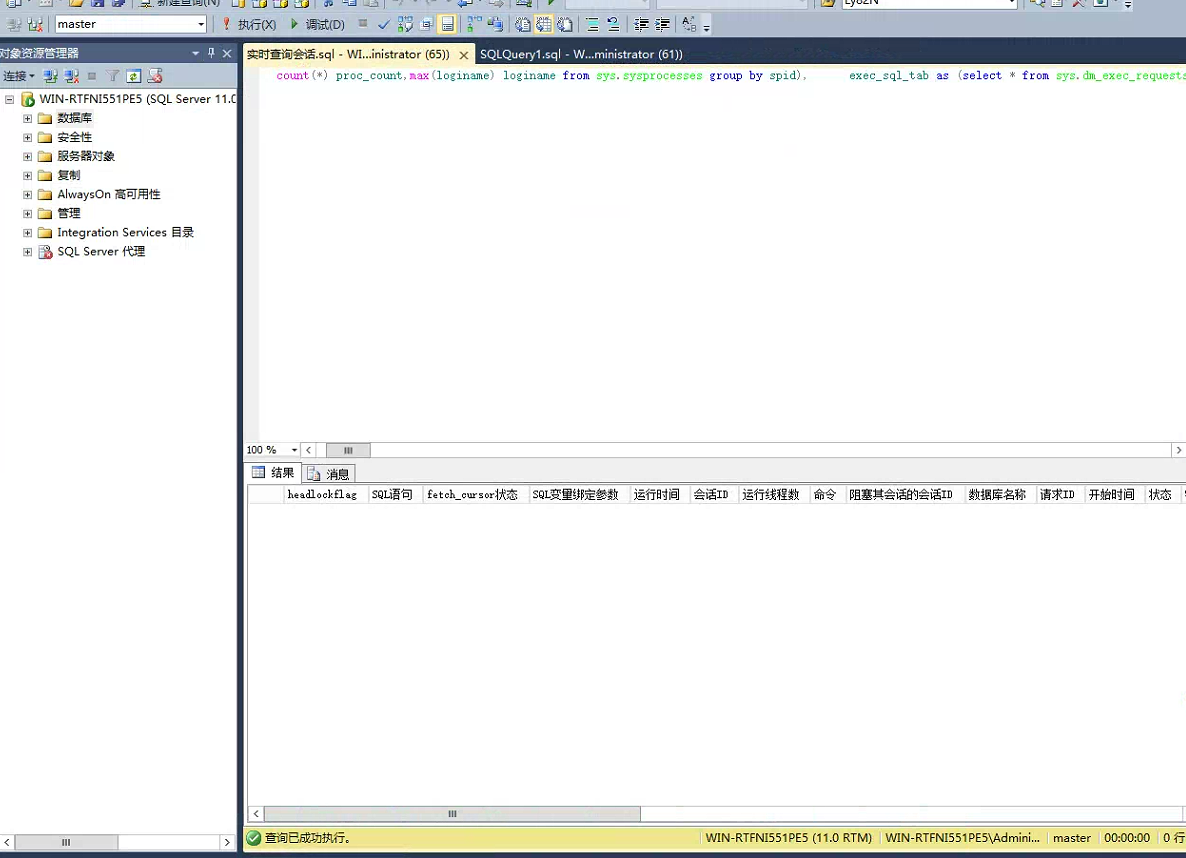
-- sqlserver 实时查询活动sql(也可以参考 https://open.seeyoncloud.com/v5doc/142/1184/318.html):
with t_proc AS (SELECT spid,count(*) proc_count,max(loginame) loginame from sys.sysprocesses group by spid), exec_sql_tab as (select * from sys.dm_exec_requests), h_lock as (select a.blocking_session_id AS blocked from exec_sql_tab a where not exists(select 1 from exec_sql_tab where blocking_session_id>0 AND session_id=a.blocking_session_id) AND blocking_session_id>0 group by a.blocking_session_id ) SELECT (case when h_lock.blocked is not null then 1 else 0 end) as 'headlockflag', '"'+(case when substring(dest.text,1,16)='FETCH API_CURSOR' then (SELECT t.text FROM sys.dm_exec_cursors (der.session_id ) c CROSS APPLY sys.dm_exec_sql_text (c.sql_handle) t) else dest.text END)+'"' AS 'SQL语句', (case when substring(dest.text,1,16)='FETCH API_CURSOR' then 1 else 0 END) AS 'fetch_cursor状态', (case when charindex('<ParameterList>',dest_plan.query_plan)>0 then '"'+substring(dest_plan.query_plan,charindex('<ParameterList>',dest_plan.query_plan), charindex('</ParameterList>',dest_plan.query_plan)-charindex('<ParameterList>',dest_plan.query_plan)+16 )+'"' else '' end) AS 'SQL变量绑定参数', der.cpu_time AS '运行时间', der.session_id as '会话ID', t_proc.proc_count as '运行线程数', der.command AS '命令', der.blocking_session_id AS '阻塞其会话的会话ID', DB_NAME(der.database_id) AS '数据库名称', der.request_id AS '请求ID', der.start_time AS '开始时间', der.status AS '状态', der.reads AS '物理读次数', der.writes AS '写次数', der.logical_reads AS '逻辑读次数', der.row_count AS '返回结果行数', der.wait_type AS '等待资源类型', der.wait_time AS '等待时间', der.total_elapsed_time, der.wait_resource AS '等待的资源', conn.client_net_address as '客户端地址', tmpdb.user_objects_alloc_page_count as 'tempdb使用页', t_proc.loginame as '登录用户名', der.query_hash as 'SQL的HASH', der.transaction_id, der.open_transaction_count, der.open_resultset_count, convert(char(24),getdate(),121) as '采集时刻' FROM exec_sql_tab der left join sys.dm_exec_connections conn on (conn.session_id = der.session_id) left join h_lock on (h_lock.blocked=der.session_id) left join t_proc on (t_proc.spid=der.session_id) left join sys.dm_db_session_space_usage tmpdb on (tmpdb.session_id=der.session_id) CROSS APPLY sys.dm_exec_sql_text(der.sql_handle) AS dest CROSS APPLY sys.dm_exec_text_query_plan(der.plan_handle,DEFAULT,DEFAULT) AS dest_plan WHERE der.session_id<> @@spid ORDER BY 'headlockflag' desc,blocking_session_id,cpu_time DESC
# 解决方法
先卸载360安全卫士,同时协调客户处理与数据库间网络延迟异常
注:服务器安装杀毒软件是必须操作,建议使用火绒杀毒软件 或 Window Defender。
编撰人:wangyxyf、het
